

The term WAF stands for Web Application Firewall.
A traditional firewall mainly operates at the network layer, filtering packets based on source IP, destination IP, source port, destination port, and protocol (TCP/UDP/ICMP). In other words, it ensures that only authorized connections reach the server, but it does not understand the content of the traffic.
The WAF, however, goes further: it is specifically designed to protect web applications. Instead of only analyzing addresses and ports, the WAF inspects the content of HTTP/HTTPS requests. This allows it to identify and block malicious access attempts that a traditional firewall would miss.
In other words, the WAF acts as a shield between the internet and your web application, blocking threats before they can cause damage.
CrowdSec is the WAF we use here at Gole.
It is an open-source, collaborative, and modern solution that not only protects your application in real time but also learns from attacks occurring elsewhere in the world.
That means: when a malicious IP is detected in one environment, the entire CrowdSec community can benefit and block that same IP.

The process is simple to understand:

helm repo add crowdsec https://crowdsecurity.github.io/helm-charts
helm repo update
helm show values crowdsec/crowdsec > crowdsec-default-values.yaml
crowdsec-default-values.yaml fileagent:
acquisition:
- namespace: traefik
podName: traefik-*
program: traefik
lapi:
env:
- name: ENROLL_KEY
value: "YOUR_ENROLL_KEY"
- name: ENROLL_INSTANCE_NAME
value: "my-k8s-cluster"
- name: ENROLL_TAGS
value: "k8s linux production"
persistentVolume:
data:
enabled: true
storageClassName: "your-storage-class-name"
size: 1Gi
config:
enabled: true
storageClassName: "your-storage-class-name"
size: 100Mi
kubectl create ns crowdsec
helm install crowdsec crowdsec/crowdsec -n crowdsec -f crowdsec-default-values.yaml
kubectl -n crowdsec exec -it crowdsec-lapi-* -- sh
cscli bouncers add traefik
apiVersion: traefik.io/v1alpha1
kind: Middleware
metadata:
name: bouncer
namespace: traefik
spec:
plugin:
bouncer:
CrowdsecLapiKey: <YOUR_API_KEY>
crowdsecLapiHost: "crowdsec-service.crowdsec.svc.cluster.local"
crowdsecLapiPort: "8080"
crowdsecAppsecHost: "crowdsec-appsec-service.crowdsec.svc.cluster.local"
crowdsecAppsecPort: "7422"
crowdsecAppsecScheme: http
Enabled: true
logLevel: DEBUG
crowdsecMode: appsec
controller:
extraInitContainers:
- name: init-clone-crowdsec-bouncer
image: crowdsecurity/lua-bouncer-plugin
env:
- name: API_URL
value: "http://crowdsec-service.crowdsec.svc.cluster.local:8080"
- name: API_KEY
value: "<API KEY>"
- name: BOUNCER_CONFIG
value: "/crowdsec/crowdsec-bouncer.conf"
appsec:
enabled: true
acquisitions:
- source: appsec
listen_addr: "0.0.0.0:7422"
path: /
appsec_config: crowdsecurity/crs-vpatch
labels:
type: appsec
env:
- name: COLLECTIONS
value: "crowdsecurity/appsec-wordpress"
The CrowdSec console has a limit of 500 alerts, which can restrict the visibility of events in high-traffic environments. For a complete and detailed monitoring, we created a Grafana dashboard that allows you to observe IP blocks, attacks, and security decisions in real-time.
This dashboard includes:
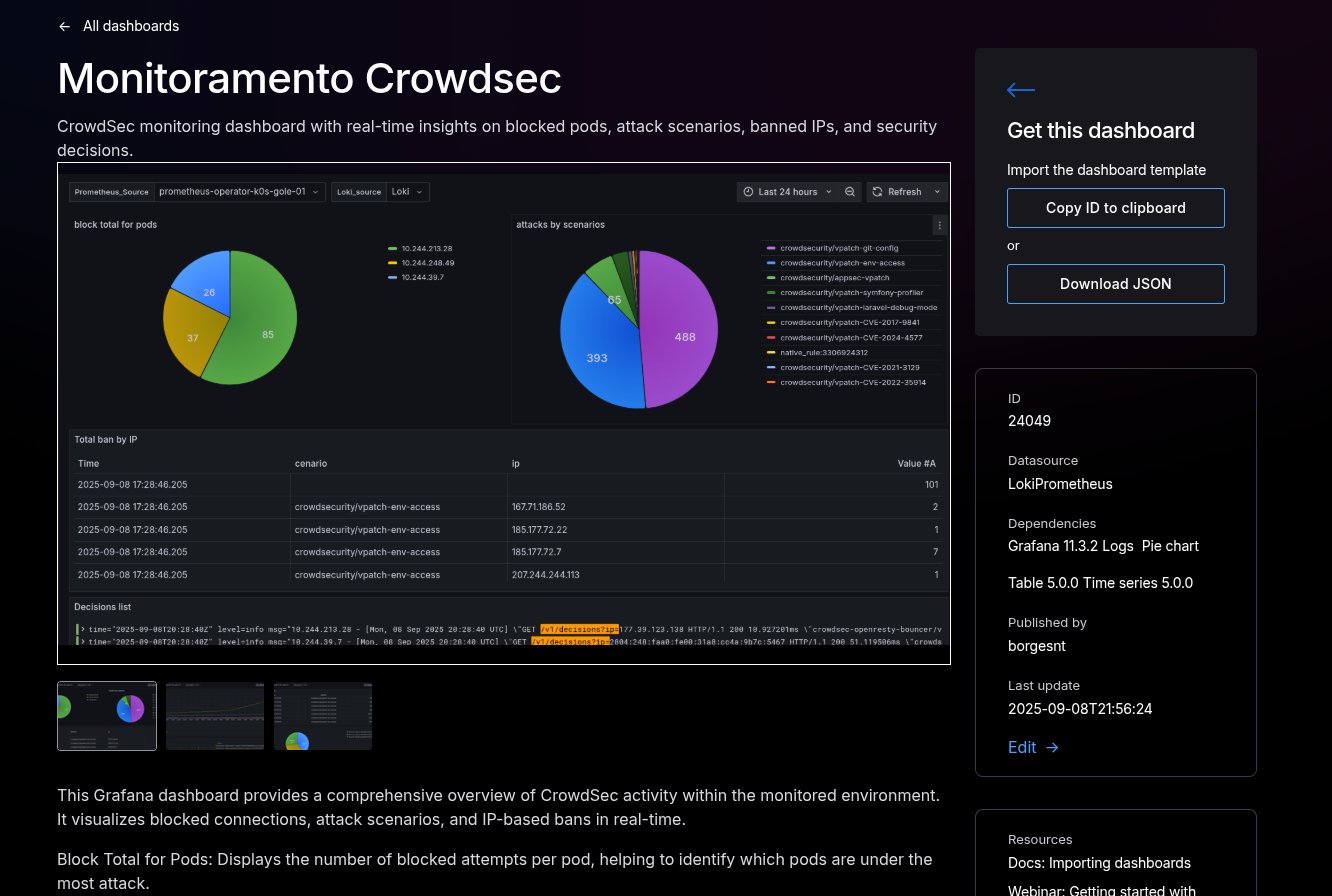
Access the dashboard: CrowdSec Monitoring on Grafana
This feature is essential for security teams to monitor, analyze, and respond quickly to threats in the infrastructure.
With these configurations, CrowdSec is integrated into your Kubernetes cluster, monitoring logs, registering instances, and protecting your applications with Traefik, Nginx, and WAF AppSec.
Access the console: https://app.crowdsec.net/security-engines